How to Protect Yourself from WannaCry Ransomware?
WannaCry or WanaCrypt0r 2.0 or Wanna Decryptor or WannaCrypt is a ransomware Trojan designed specifically to target Microsoft Windows operating system. The attack begin to appear on Friday, 12 May 2017. The attack was mounted on a unprecedented scale that it infects around 2.5 million reported computers worldwide and numbers are growing ever since.
WannaCry uses Eternalblue a zero day exploit for Microsoft Windows Server Message Block (SMB) component. This exploits was used by NSA and recently exposed by The Shadow Broker group. The WannaCry authors demands Bitcoins worth $300 to $600. The impact of this ransomeware was so horrifying that Microsoft releases a patch of it long forgotten operating systems Windows XP patch. This vulnerability has a CVE-2017-0147 number. This vulnerability was fixed in Microsoft Security Bulletin MS17-010. In order you to protect yourself from this do the followings to your PC or a Laptop.
Windows 10 is immune to WannaCry or its derivatives attack,yet.
If you disable SMB from windows many windows features will not work properly, so it is best to install the patch provided by the Microsoft. Click on this link and find right patch and install it. If you are unsure how to do it, simple run the windows update service which will install the appropriate updates automatically. To do that open command window as an administrator and run the following command
Go to Control Panel → Programs → Turn Windows features on and off.
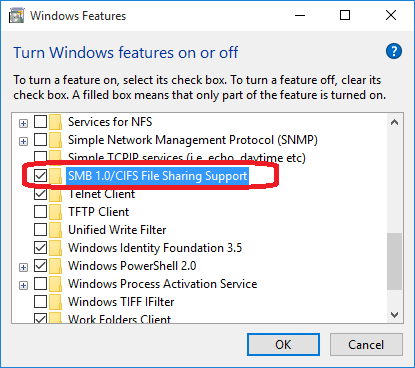
Turn Off the SMB 1.0/CIFS File Sharing Support by un-checking the checkbox and restart your system.
Windows 10 is immune to WannaCry or its derivatives attack,yet.
If you disable SMB from windows many windows features will not work properly, so it is best to install the patch provided by the Microsoft. Click on this link and find right patch and install it. If you are unsure how to do it, simple run the windows update service which will install the appropriate updates automatically. To do that open command window as an administrator and run the following command
wuauclt.exe /detectnow /updatenowIf you cannot install update make sure Windows Defender signatures are up to date. For more information what service are effected by disabling SMB can be found here
Windows 8.1 and Windows Server 2012 R2 and above
For Windows Server 8.1 and Windows Server 2012 R2 and above SMB can be gracefully Turn off using the following procedure.Go to Control Panel → Programs → Turn Windows features on and off.

Turn Off the SMB 1.0/CIFS File Sharing Support by un-checking the checkbox and restart your system.
WannaCry Snort Rules for Network Administrators
If you are network administrator add the following rules to your SNORT Firewall to stop infecting and propagating WannaCry.alert tcp $HOME_NET 445 -> any any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response”; flow:from_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:2;) alert smb any any -> $HOME_NET any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Request (set)”; flow:to_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 18 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:set,ETPRO.ETERNALBLUE; flowbits:noalert; classtype:trojan-activity; sid:2024220; rev:1;) alert smb $HOME_NET any -> any any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response”; flow:from_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:1;)
Click to Load Comments

