RokRAT Adobe Flash Malware Sample (CVE-2018-4878)
RokRAT exploits CVE-2018-4878, a Adobe Falsh 0-day vulnerability. Its is believed to be the work of supposedly North Korean Group 123 or APT37. RokRAT is disseminated via a excel file which has an ActiveX Object, that object is an embedded SWF file.
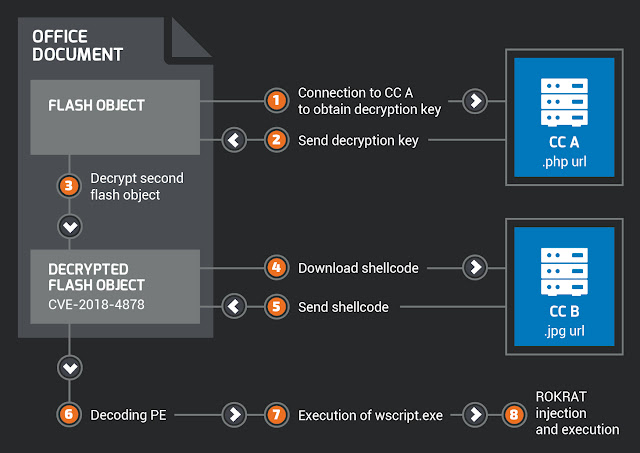
 The embedded SWF object exploits Flash's Zero-day Use After Free (UAF) vulnerability identified by CVE-2018-4878. When then contact its command and control (C&C) server for shell codes which then will be executed in the memory. VirusTotal report of RokRAT can be found here. RokRAT execution flow is depicted in following image.
The embedded SWF object exploits Flash's Zero-day Use After Free (UAF) vulnerability identified by CVE-2018-4878. When then contact its command and control (C&C) server for shell codes which then will be executed in the memory. VirusTotal report of RokRAT can be found here. RokRAT execution flow is depicted in following image.
 The password of the zip is: infected
The password of the zip is: infected
 The embedded SWF object exploits Flash's Zero-day Use After Free (UAF) vulnerability identified by CVE-2018-4878. When then contact its command and control (C&C) server for shell codes which then will be executed in the memory. VirusTotal report of RokRAT can be found here. RokRAT execution flow is depicted in following image.
The embedded SWF object exploits Flash's Zero-day Use After Free (UAF) vulnerability identified by CVE-2018-4878. When then contact its command and control (C&C) server for shell codes which then will be executed in the memory. VirusTotal report of RokRAT can be found here. RokRAT execution flow is depicted in following image.

RokRAT Malware Sample Hash
MD5: d2881e56e66aeaebef7efaa60a58ef9b SHA1: c09c1be69e5a206bcfe3d726773f0b0ddecb3622 SHA256: e1546323dc746ed2f7a5c973dcecc79b014b68bdd8a6230239283b4f775f4bbd SSDEEP: 12288:cbeQy0+6dUlyAcdqfAkMvGpns9gKYLd+NjhzZkZf7:AfuJGv2ns9XRkZf
Dowload RokRAT Malware Sample
 The password of the zip is: infected
The password of the zip is: infected
Click to Load Comments







